Prove that you are Cybersecure
September 04, 2020
Cyber Security
With this post, we're taking a hint that you (our readers) have been sending us. We've had an increasing number of readers arrive at our site after searching for how to "prove" that you are cybersecure. And, we get it. As small business owners and operators, it's totally normal for a larger organization (an enterprise client, a bank, an investor, a partner) to ask you to "prove it" when you make a claim. And the fact that you are hunting around the web to find a way to prove it, means that we need to talk about that topic more on this blog.
So, let's talk about how you can fulfill that: how you can "prove" that you are cybersecure.
If you don't know where you want to go...
You remember the old quote from Lewis Carroll, right?
“If you don't know where you want to go, then it doesn't matter which path you take.”
We think that's a good phrase to have in mind when you think about the very first step towards proving that you are cybersecure. Specifically, we suggest to start by thinking about (reviewing, drafting, editing, etc), your set of cybersecurity policies and plans. These policies and plans describe where you want to go. Are you a company that embraces remote work and empowers employees with tools to make that remote work environment safe? Are you a company where all information needs to stay locked inside the four walls of your building? Are you a hybrid where employees can come and go as they please, as long as they follow the ground rules of cybersecurity wherever they go?
Your policies set the stage for everything that happens next. Oh, and if you don't have any policies or plans in place, or are dissatisfied with the ones you've got, let us know. We've got a Policy Manager engine that will ask you a few simple questions and generate a set of battle-tested cybersecurity policies that make for a great (and credible) start.
Is it Just "On Paper"?
If you've been asked this question before, it probably wasn't pleasant to hear. A question that gets asked about cybersecurity policies -- especially when enterprises are vetting small businesses -- is around the extent to which a (sometimes fancy) written policy is actually/really followed. You know what we mean. The policy makes an elaborate statement about the companies controls that guard against phishing attacks, for example. Does your team actually undergo recurring cybersecurity phishing training? Phishing simulations? What about DNS filtering? Monitoring of look-a-like domains?
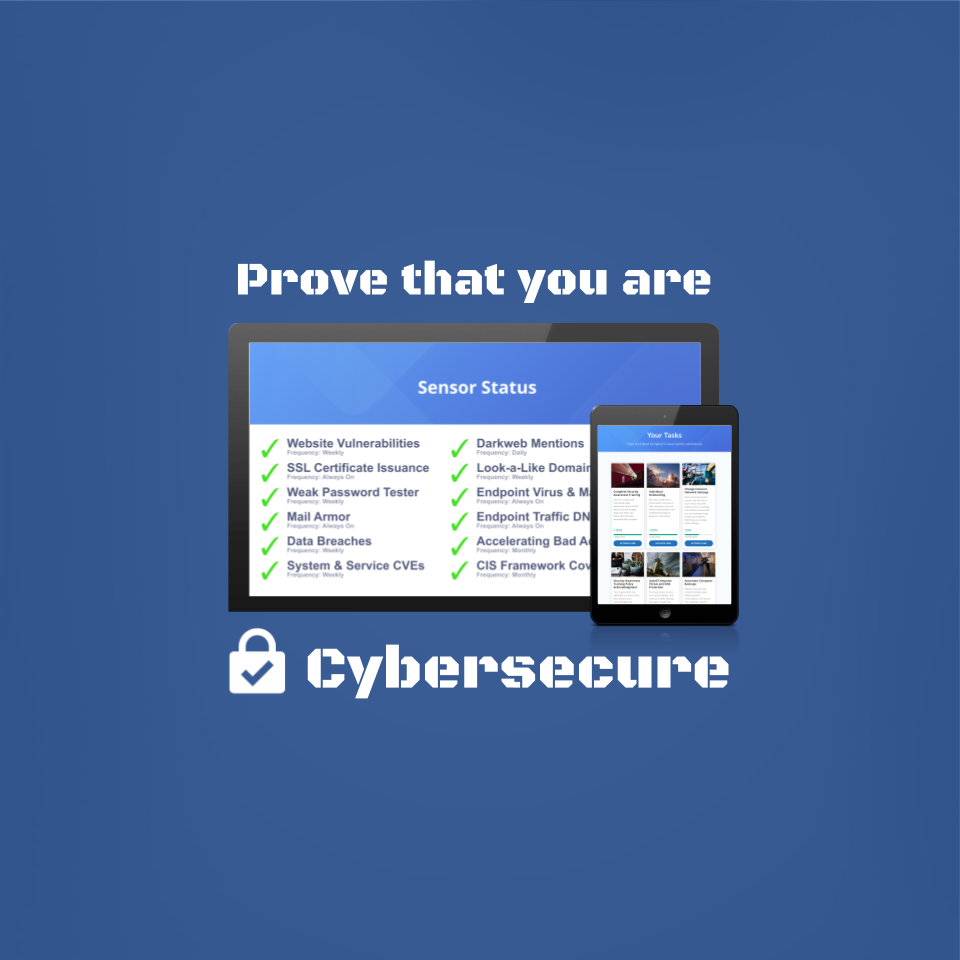
The situation you don't want to be in, is to be hoping/wishing that no one ever asks you whether a particular part of the policy is followed. That's wishful thinking. Although this blog post isn't a commercial for Havoc Shield, suffice it to say that when you use our Policy Manager to establish cybersecurity policies, the very next place we take you is to kick off the rollout of processes and tools to your team, to make the policies real. Often, the policies that our customers adopt, lead us into orchestrating the rollout of several of the following cybersecurity sensors:

These sensors are proactive measures that allow you to stay a step ahead. For example, when employees from your company are found in a data breach of a 3rd party website, it's much better to know that promptly, than to find out when some difficult-to-remediate additional damage is done. That's a big part of being cybersecure.
If your cybersecurity program includes the implementation of sensors and tools like the above, there is a good chance that your company is the type of place where the policies are actually followed in a meaningful way. If any of the above sensors or tools are unfamiliar to you, it might be time to raise your cybersecurity game (we're here to help).
You are Cybersecure? Prove It.
Ok, so we set out to talk about how to prove that you are cybersecure. Let's circle all the way back to that topic now. You've got policies and plans. You've got cybersecurity sensors for proactive cyber threat identification. You've got tools and processes that map to the policies and plans, and are in actual (real!) use. Not just in some policy somewhere.
If that all describes you and your situation, congratulations. You've earned the right to confidently "prove it" when an enterprise, investor, or other stakeholder asks for evidence that you have a robust cybersecurity posture.
The most common "prove it" requests that we help clients field, include:
- Requests for Policies: requests to inspect copies of your various policies
- Requests for Audit Logs: requests that illustrate that the policies are actually being followed, for example, an audit log showing the timestamp of every employee's completion of cybersecurity training, or the timestamp of every employee's acknowledgement of a particular policy.
- Attestation Letters: independent third party letters that describe your cybersecurity program and are treated as independent evidence that you are following the policies you adopt. Havoc Shield has an attestation letter generator built into our platform for this exact purpose, since it's become such a common request.
If after reading this article you feel well positioned to "prove it" when someone asks, congratulations! If, however, this article revealed some gaps in your policies/plans, implementation, or ability to prove your cybersecurity posture, please get in touch. We'd be glad to help.